Use four terminals to connect to the four hosts.
(from terminal 1) $ docker-compose exec firewall bash (from terminal 2) $ docker-compose exec host1 bash (from terminal 3) $ docker-compose exec host2 bash (from terminal 4) $ docker-compose exec host3 bash
You can inspect the network interfaces on each hosts using ifconfig . As described in the prerequisites, firewall has three network interfaces (plus the internal loopback):
firewall # ifconfig
eth0 Link encap:Ethernet HWaddr 02:42:AC:1A:00:02
inet addr:172.25.0.2 Bcast:172.25.255.255 Mask:255.255.0.0
...
eth1 Link encap:Ethernet HWaddr 02:42:AC:1E:00:01
inet addr:172.30.0.2 Bcast:172.30.255.255 Mask:255.255.0.0
...
eth2 Link encap:Ethernet HWaddr 02:42:AC:23:00:01
inet addr:172.31.0.2 Bcast:172.31.255.255 Mask:255.255.0.0
...
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
...
Explanation:
eth0connects the firewall to the docker host and to the Internet. This represents the external IP address of the firewall (172.25.0.2)eth1is connected to the172.30.0.0/16subnet with IP172.30.0.2eth2is connected to the172.31.0.0/16subnet with IP172.31.0.2lois the loopback interface, for local connections
Check connectivity: ping
We now use ping to check connectivity between the hosts.
firewall # ping 172.30.0.10 PING 172.30.0.10 (172.30.0.10): 56 data bytes 64 bytes from 172.30.0.10: seq=0 ttl=64 time=0.217 ms 64 bytes from 172.30.0.10: seq=1 ttl=64 time=0.179 ms
Exercise
Check that every host can reach (ping) any other host.
netfilter tables, chains and default policy
iptables is a user-space utility that interacts with the netfilter framework in the linux kernel and controls the firewall configuration.
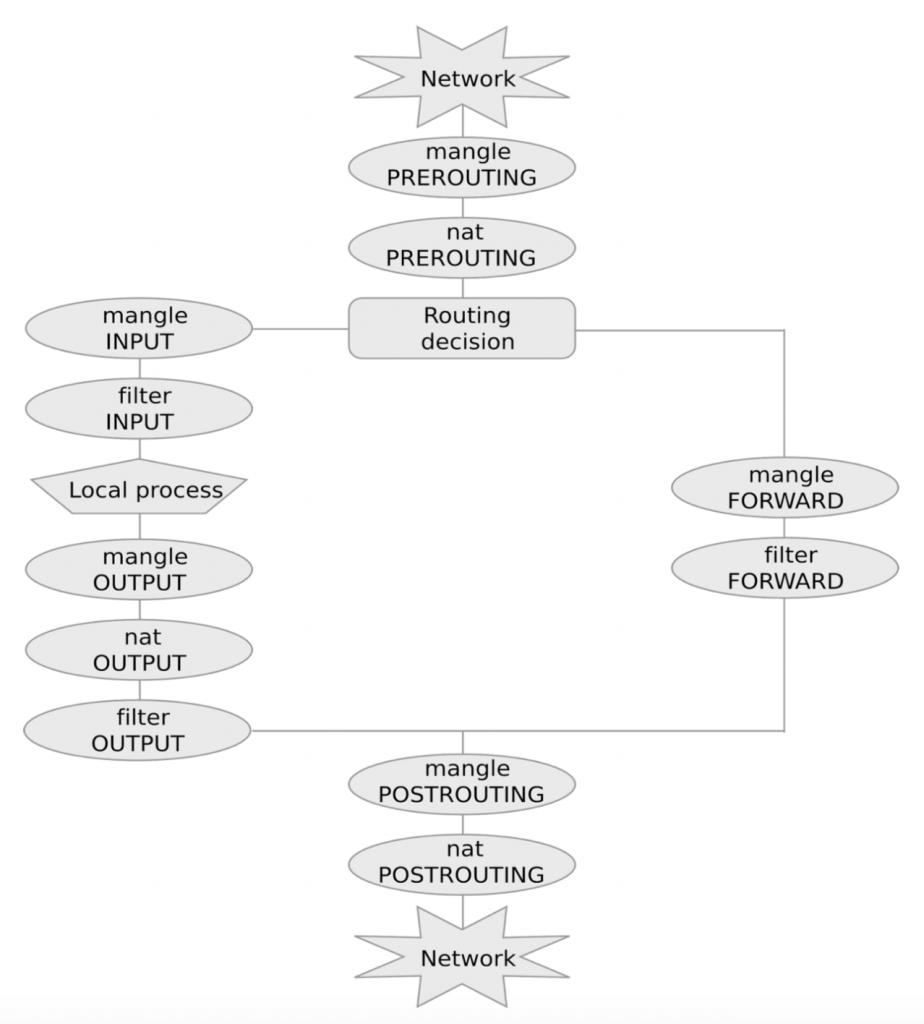
As discussed in the previous class, netfilter is based on tables each containing lists of rules called chains. The three most commonly used tables are:
filterfor packet filteringnatfor NATsmanglefor packet alteration
Chains are lists of rules that are inspected one after the other. There are five predefined chains that are inspected in specific moments of a packet life cycle:
PREROUTING, as soon as the packet reaches the hostFORWARD, when the packet is routed through the hostPOSTROUTING, when the packet is about to leave the hostINPUT, when packets are routed to the hostOUTPUT, when packets are generated by the host
Each chain contains zero or more rules, that are inspected sequentially. If the packet matches the rule then it is processed as specified in the rule target. If instead the rule is not matched, the next rule in the chain is examined.
The most commonly used targets are:
ACCEPT, for accepting the packetDROP, for dropping itDNAT, for destination NATSNATfor source NAT
A default policy is triggered if none of the rules in the chain matches.
Exercise
Suppose that the firewall is forwarding a packet coming from host h1 to host h2. What chains of tables nat and filter are inspected?
List them in order of inspection in the format (table,CHAIN),(table,CHAIN),… the answer is the password for Task 2! (use lowercase for tables and uppercase for chains, as in the description above)
