So far, we have seen simple historical ciphers and we have discussed how to break them. Modern ciphers, however, are based on very simple operations, such as substitution, xor, …, that are combined in a smart way so to make the overall algorithm strong and really hard to analyse. It is important to keep in mind that combining simple ciphers does not always improve security. For example, consider the shift cipher composed twice. We first shift by k1 and then by k2 modulo 26.
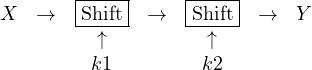
It is clear that this is equivalent to shifting by k1+k2 modulo 26, meaning that applying twice the cipher is the same as applying it once with a key given by the sum of the two keys.
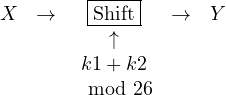
This informal reasoning can be made more precise.
Definition (Composition). We consider two ciphers ![]() and
and ![]() . We let
. We let ![]() , that we note as
, that we note as ![]() and
and ![]() in the following. In this way the output of one cipher is for sure a possible plaintext for the second cipher. We can now define composition as
in the following. In this way the output of one cipher is for sure a possible plaintext for the second cipher. We can now define composition as ![]() with
with
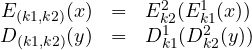
Example. Consider the composition of the two shifts above. Formally we have that ![]() . Thus,
. Thus,
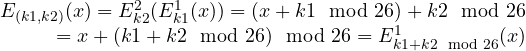
This proves that composing the shift cipher twice is equivalent to applying it once using as a key the sum of the two keys k1 and k2.
Exercise. Show that the composition of the shift cipher with the substitution cipher is still a substitution cipher with a different key. Give a constructive way to derive the new key. What happens if substitution is applied before shift?
Exercise. Consider the composition of Vigenére cipher with key ALICE with the shift cipher with key 8. Is the resulting cipher equivalent to a known one? If so, what is the resulting key?
Idempotent ciphers
We have seen that the shift cipher, when repeated twice is equivalent to itself with a different key. When this happens, the cipher ![]() is said to be idempotent, written
is said to be idempotent, written ![]() . In this case we know that iterating the cipher will be of no use to improve its security. Even if we repeat it n times we will still get the initial cipher, i.e.,
. In this case we know that iterating the cipher will be of no use to improve its security. Even if we repeat it n times we will still get the initial cipher, i.e., ![]() .
.
We have mentioned that modern ciphers are based on simple operations composed together. Another ingredient is, in fact, iteration. Almost any modern cipher repeats a basic core of operations for a certain number of rounds. It is thus necessary that such core operations do not constitute an idempotent cipher.
It can be proved that if we have two idempotent ciphers that commute, i.e., such that ![]() , then their composition is also idempotent. In this case, we know that iterating their composition is useless. To see why this holds consider one iteration of their composition (recall that function composition is associative):
, then their composition is also idempotent. In this case, we know that iterating their composition is useless. To see why this holds consider one iteration of their composition (recall that function composition is associative):

Exercise. Apply the above result to show that the composition of Vigenére and the shift cipher is idempotent.
Lesson learned
We have seen examples of how algebraic properties, such as commutativity, can help simplifying the analysis of a cipher. When developing a robust cipher we need to avoid as much as possible that operations can be rearranged, swapped, simplified.
